@dblackshell wrote about a
"nifty" feature on his blog a while back. A website he uses has implemented a feature which will alert the end user if their flash version is not up to date. It delivers the message in a very authoritative looking way, as you can see in this image (click for full version).
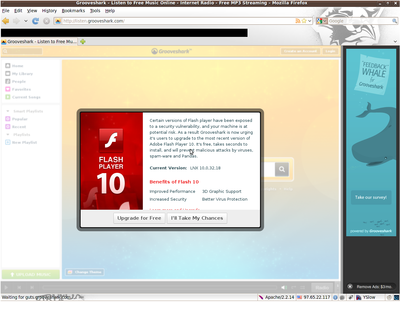
I tend to disagree with his opinion. It is not "nifty",
it is harmful. Although I won't go in depth here, I believe as many other do that user education does not work. Casual computer users does not have the required knowledge to determine the validity of this message at the tip of their fingers. The end result is that we train more users to click accept. What do you think this user will do the next time they are presented with this image?
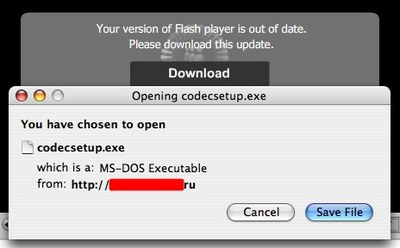
The latter image is
malware disguised as a flash update. Could your parents, grand parents aunts, cousins or friends tell the difference?